A proactive and efficient incident response plan is essential for mitigating the impact of security breaches and protecting your organisation’s critical assets. At CISO Online™, we offer comprehensive incident response services designed to swiftly address and manage cyber incidents, minimising damage and ensuring a quick recovery. Our team of experts is equipped to handle all aspects of incident response, providing you with peace of mind and robust protection against the unexpected.
Protect your organisation with expert incident response services. Contact us today to develop a tailored incident response plan and ensure your business is prepared for any cyber threat

Without a structured incident response strategy, the aftermath of a cyber attack can be chaotic and costly. Delayed response times can exacerbate the impact of the breach, allowing attackers to cause further damage. Furthermore, the lack of a clear action plan can lead to confusion among your team, making it difficult to contain and mitigate the threat effectively.
At CISO Online™, we specialise in providing comprehensive incident response services tailored to your business needs. Our team of experts is equipped to handle all aspects of incident response, from immediate threat containment to post-incident analysis. We ensure that your organisation can quickly recover from cyber attacks and strengthen its defenses against future threat
Without a structured incident response strategy, the aftermath of a cyber attack can be chaotic and costly. Delayed response times can exacerbate the impact of the breach, allowing attackers to cause further damage. Furthermore, the lack of a clear action plan can lead to confusion among your team, making it difficult to contain and mitigate the threat effectively.
At CISO Online™, we specialise in providing comprehensive incident response services tailored to your business needs. Our team of experts is equipped to handle all aspects of incident response, from immediate threat containment to post-incident analysis. We ensure that your organisation can quickly recover from cyber attacks and strengthen its defenses against future threat
Ready to safeguard your business with expert incident response services? contact us today to develop a robust incident response plan tailored to your needs!


Cyber attacks can be overwhelming, but handling them doesn’t have to be. Without a proper incident response plan, your business risks significant data breaches, financial losses, and reputational harm. The longer it takes to respond to a threat, the greater the potential damage.
At CISO Online™, we’re here to help you stay ahead of cyber threats with our quick and reliable incident response services. We’ll work with you to create a customised response plan that fits your business, ensuring you can swiftly handle any security breaches. Our friendly and knowledgeable team will guide you through every step of the process, so you can focus on running your business while we take care of your cybersecurity needs.
Don’t wait until it’s too late. reach out to us today and let us help you protect your business with our expert incident response services!
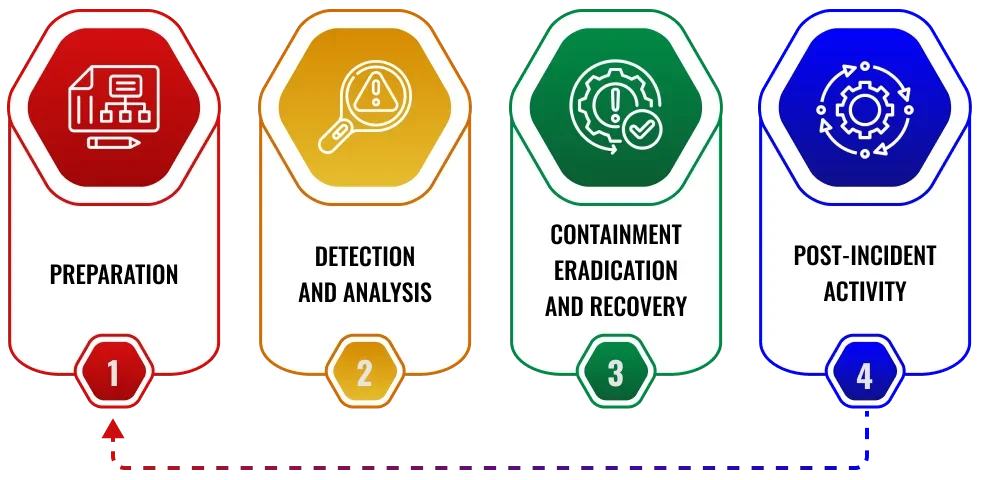

At CISO Online™, our Incident Response Process is meticulously designed to navigate and mitigate cybersecurity incidents with precision and expertise. Our approach ensures thorough handling from initial assessment to transformative measures, fortifying your organisation’s cybersecurity posture for the future.
With CISO Online™, you’re choosing a partner dedicated to guiding you through the complexities of digital threats. Our services in Digital Forensics and Incident Response are not just about managing the crisis; they’re about turning adversity into strength. We ensure that your organisation emerges from incidents more resilient and better prepared for the challenges of the digital age.
Embark on a journey to enhanced digital security with CISO Online, where expert analysis meets strategic recovery, ensuring your organisation is fortified today and ready for tomorrow.
Experience the Difference Today!
Incident response is a structured approach to handling and managing the aftermath of a security breach or cyber attack. Its goal is to handle the situation in a way that limits damage and reduces recovery time and costs.
Incident response is crucial because it helps organisations quickly address and mitigate security incidents, reducing potential damage, data loss, and downtime. A well-prepared response can save businesses significant costs and protect their reputation.
The key steps in an incident response plan typically include preparation, identification, containment, eradication, recovery, and lessons learned. Each step is essential for effectively managing and resolving incidents.
Every business, regardless of size or industry, should have an incident response plan. If your business handles sensitive data or relies on digital systems, having a plan in place is essential to quickly and effectively respond to security incidents.
An incident response plan should include roles and responsibilities, communication strategies, detailed procedures for each response phase, and protocols for documentation and reporting. It should also include contact information for key personnel and external partners.
An incident response team should include IT staff, cybersecurity experts, legal advisors, communications personnel, and senior management. Depending on the incident, other specialists may also be involved, such as HR or public relations professionals.
Your incident response plan should be reviewed and updated at least annually or after any significant change in your organisation’s IT infrastructure, business processes, or after a major security incident.
Common types of security incidents include malware infections, phishing attacks, data breaches, unauthorised access, denial of service attacks, and insider threats. Each type requires a specific response strategy.
Regular testing through tabletop exercises, simulations, and full-scale drills is essential. These tests help ensure that team members are familiar with their roles and that the plan works as intended under various scenarios.
Effective communication is critical in incident response. It involves informing stakeholders, coordinating with team members, and providing clear instructions. Good communication can help contain the incident and mitigate its impact.
Your incident response plan should address legal and regulatory requirements, including notification obligations and data protection laws. Legal advisors should be part of your incident response team to guide these efforts.
Incident response focuses on managing and mitigating security incidents, while disaster recovery is about restoring systems and data after a catastrophic event. Both are essential for comprehensive business continuity planning.
Yes, many organisations choose to outsource incident response to specialised service providers. These providers offer expertise, resources, and tools that may not be available in-house, ensuring a more effective response.
Incident response tools include security information and event management (SIEM) systems, intrusion detection systems (IDS), endpoint detection and response (EDR) tools, and forensic analysis software. These tools help detect, analyse, and respond to security incidents.
Improving incident response capabilities involves regular training, updating the response plan, conducting simulations, investing in advanced security tools, and learning from past incidents. Continuous improvement is key to staying prepared for evolving threats.

