Take the first step towards strengthening your organisation’s security posture today.

KnowBe4
Enhance Your Cybersecurity Awareness with KnowBe4 Partnership
Partnering with KnowBe4, CISO Online™ delivers cutting-edge User Awareness Training to empower your team against cyber threats. Leveraging KnowBe4’s expertise and resources, we provide comprehensive training programs designed to equip your employees with the knowledge and skills needed to recognise and respond to cybersecurity risks effectively.
Benefits:
KnowBe4 is the world’s largest integrated platform for security awareness training combined with simulated phishing attacks.
Join the more than 65,000 customers fighting the growing problem of social engineering.






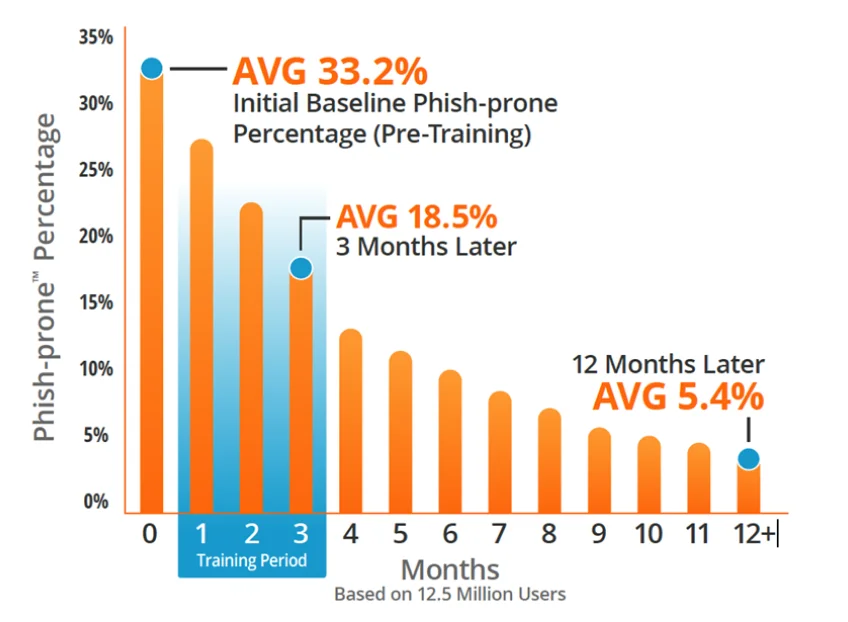
SEE THE RESULTS
SEE THE RESULTS
Training Library and Simulated Phishing Content





Mobile-First Modules are optimisedto be viewed and interacted with on a mobile device.These modules are no longer than five minutesand are designed to engage users; whetherwhile they’re on the go or located in low-bandwidth regions. Mobile-First Modules are brandable and SCORM-Compliant, so they can be downloaded for use with your own LMS.




Games can reinforce the skills and information that your users are learning in a new and interesting way. Games are SCORM-Compliant and can be downloaded for use with your own LMS.




Posters and artwork are high-quality images and PDFs that can be printed or shared digitally with your users. We encourage you to hang posters within your office or distribute them to your employees’ home offices to act as a visual reminder to keep security in mind during everyday tasks.

Want to know more?
01
Training Access Level I provides you with the fundamental elements required to begin a security awareness training program
It’s ideal for organisations that do not have security awareness training in place and want to start at least an annual training program. You get training and video modules, assessments,
and educational reinforcements such as security documents and posters. We see many customers get started with Level I so their users get the basics of security awareness, including understanding what social engineering is, and then find they are ready to move to the next level of training content that takes a deeper dive into other cybersecurity topics. When annual training is no longer sufficient and you are ready to launch more frequent training campaigns, the Training Access Levels II and III set you on a path to develop a more robust and fully mature security awareness training program
02
GOLD & PLATINUM
The Training Access Level II library builds on Level I and expands to provide a greater variety in training content styles, formats, and topics. From animation, to live action, to self-paced learning, Level II unlocks the potential for you to offer more targeted training
based on your users’ roles, their location around the world, and your organisation’s industry. And, with an assortment of bite-sized training modules that are 5 minutes or less, it’s easy to set up a more frequent cadence of training campaigns that keep your users engaged. More training more often can help drive behavior change with security awareness top of mind.
03
DIAMOND
Training Access Level III includes all the training content in Levels I and II, plus access to the most comprehensive library of security awareness training content, enhancing your organisation’s ability to deliver a fully mature awareness program on an ongoing basis.
Level III includes multiple award-winning streaming-quality video series that tie scenes from each episode to key cybersecurity best practices
making learning how to make smarter security decisions via real-world applications fun and engaging.
With a wide array of topics, formats, lengths, and styles from multiple content publishers, you have more content options to meet the unique needs of your users and align with your organisation’s corporate culture. With Level III, you can experiment with different styles and formats to different audience segments to maximize user engagement. This level also gives you the flexibility to mix things up to hone in on what content resonates best across different departments and regional locations. You can create shorter and more frequent training campaigns that make it easier to deploy your awareness program all year long.
Keep your learners engaged with a consistent cadence of campaigns using a variety of content on security best practices. This mix of fresh content will build muscle memory over time without using the same training over and over again.
01
Training Access Level I provides you with the fundamental elements required to begin a security awareness training program
It’s ideal for organisations that do not have security awareness training in place and want to start at least an annual training program. You get training and video modules, assessments,
and educational reinforcements such as security documents and posters. We see many customers get started with Level I so their users get the basics of security awareness, including understanding what social engineering is, and then find they are ready to move to the next level of training content that takes a deeper dive into other cybersecurity topics. When annual training is no longer sufficient and you are ready to launch more frequent training campaigns, the Training Access Levels II and III set you on a path to develop a more robust and fully mature security awareness training program
based on your users’ roles, their location around the world, and your organisation’s industry. And, with an assortment of bite-sized training modules that are 5 minutes or less, it’s easy to set up a more frequent cadence of training campaigns that keep your users engaged. More training more often can help drive behavior change with security awareness top of mind.
03
Training Access Level III includes all the training content in Levels I and II, plus access to the most comprehensive library of security awareness training content, enhancing your organisation’s ability to deliver a fully mature awareness program on an ongoing basis.
Level III includes multiple award-winning streaming-quality video series that tie scenes from each episode to key cybersecurity best practices
making learning how to make smarter security decisions via real-world applications fun and engaging.
With a wide array of topics, formats, lengths, and styles from multiple content publishers, you have more content options to meet the unique needs of your users and align with your organisation’s corporate culture. With Level III, you can experiment with different styles and formats to different audience segments to maximize user engagement. This level also gives you the flexibility to mix things up to hone in on what content resonates best across different departments and regional locations. You can create shorter and more frequent training campaigns that make it easier to deploy your awareness program all year long.
Keep your learners engaged with a consistent cadence of campaigns using a variety of content on security best practices. This mix of fresh content will build muscle memory over time without using the same training over and over again.
Ready to level up your awareness?

Cybersecurity awareness training is an educational program designed to inform employees about cybersecurity threats, safe practices, and the importance of following security policies. Its goal is to reduce the risk of human error leading to security incidents.
Reduce Risk: Helps prevent common security breaches caused by human error.
Compliance: Meets regulatory and industry requirements for employee training.
Incident Response: Empowers employees to recognise and report potential security incidents.
Culture of Security: Fosters a security-conscious culture within the organisation.
Protect Assets: Ensures the safety of sensitive data and IT systems.
All employees, contractors, and third-party partners with access to the organisation’s IT systems and data should participate in cybersecurity awareness training. This includes executives, managers, and technical staff.
Phishing and Social Engineering: How to recognise and avoid phishing scams and social engineering attacks.
Password Security: Best practices for creating and managing strong passwords.
Email and Internet Use: Safe browsing habits and email security protocols.
Data Protection: How to handle sensitive information securely.
Mobile Security: Protecting mobile devices and data on the go.
Incident Reporting: Procedures for reporting suspicious activities or security incidents.
Physical Security: Safeguarding physical access to systems and devices.
Compliance Requirements: Understanding relevant laws and regulations.
Initial Training: Upon hire, all employees should receive cybersecurity training.
Regular Updates: Training should be conducted at least annually.
Ongoing Reinforcement: Regular updates and refreshers, such as monthly or quarterly, to keep employees informed about the latest threats and best practices.
Ad-Hoc Training: Additional training sessions following significant security incidents or changes in policies and procedures.
Online Courses: Interactive e-learning modules that employees can complete at their own pace.
In-Person Workshops: Classroom-style sessions led by security experts.
Webinars: Live or recorded sessions accessible remotely.
Email Newsletters: Regular updates and tips sent via email.
Posters and Infographics: Visual reminders placed around the workplace.
Simulated Phishing Tests: Practical exercises to test employees' ability to recognise phishing attempts.
Pre- and Post-Training Assessments: Tests to gauge knowledge before and after training sessions.
Phishing Simulations: Track the success rate of employees recognising and reporting simulated phishing emails.
Incident Reports: Monitor the number and quality of security incident reports before and after training.
Surveys and Feedback: Collect feedback from participants on the training’s relevance and effectiveness.
Compliance Rates: Measure adherence to security policies and procedures.
Engagement: Keeping employees interested and engaged in training content.
Consistency: Ensuring training is delivered consistently across the organisation.
Relevance: Making training content relevant to different roles and departments.
Retention: Ensuring employees retain and apply what they have learned.
Tracking Progress: Monitoring participation and completion rates.
Interactive Content: Use quizzes, games, and simulations to make learning more interactive.
Real-World Scenarios: Provide examples and case studies that are relevant to employees' roles.
Gamification: Implement a rewards system for completing training modules or recognising top performers.
Short, Focused Sessions: Break training into shorter, manageable sessions to maintain attention.
Regular Updates: Keep content current and relevant by updating it regularly to reflect the latest threats and best practices.
Support and Endorsement: Leadership should endorse and actively support the training program.
Leading by Example: Executives and managers should participate in training to set an example.
Resource Allocation: Ensure adequate resources are allocated for comprehensive training programs.
Policy Enforcement: Support the enforcement of security policies and procedures reinforced by training.
While training significantly reduces the risk of human error and improves overall security awareness, it cannot prevent all cyber threats. It should be part of a broader cybersecurity strategy that includes technical controls, policies, and incident response plans.
Risk Mitigation: Training reduces human error, a common factor in security incidents.
Policy Reinforcement: Ensures employees understand and follow security policies.
Incident Response: Prepares employees to recognise and report security incidents promptly.
Continuous Improvement: Regular training sessions help keep security practices up to date with evolving threats.
Reduced Incidents: Fewer security breaches caused by human error.
Improved Compliance: Meets regulatory requirements for security training.
Enhanced Security Culture: Creates a culture where security is a shared responsibility.
Employee Empowerment: Empowers employees to take an active role in protecting the organisation’s assets.
Cost Savings: Reduces the potential financial impact of security incidents.

