
In today’s digital landscape, safeguarding applications is essential for protecting sensitive data and mitigating cyber threats. Application security is crucial because it protects sensitive data from breaches and unauthorized access, ensuring user privacy and trust. Effective security measures prevent costly incidents and maintain business continuity by safeguarding against disruptions.
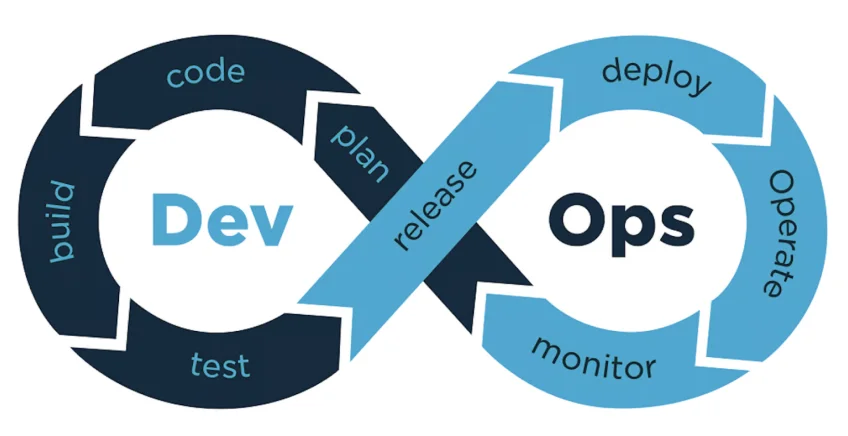
At CISO Online™, we recognise the critical need for advanced application security solutions tailored to the unique demands of the modern digital era. Our primary focus is on developing best DevSecOps practice of integrating security into every phase of the software development lifecycle, from initial design through integration, testing, deployment, and delivery. It extends the DevOps philosophy of collaboration between development and operations teams to include security teams, fostering a culture where security is a shared responsibility. This approach helps in identifying and addressing security issues early in the development process, thereby reducing vulnerabilities and ensuring compliance with security testing standards such as SAST and DAST testing.

DevSecOps ultimately aims to create a security-focused culture where security considerations and testings are an integral part of the development process, ensuring that applications are secure by design and throughout their lifecycle. This includes getting vulnerability assessment report, doing SAST and DAST testings and conducting penetration testing into right phase of the software development lifecycle.
Choosing to partner with CISO Online™ signifies a commitment to safeguarding the security and confidentiality of your applications. Our tailored solutions and comprehensive approach ensure ongoing protection against emerging threats, and unauthorised access. With CISO Online™ as your trusted partner, you can be confident that your applications are shielded from harm, offering peace of mind.
Is your business or organisation feeling overwhelmed by the complexities of application security solutions and testings? CISO Online is here to alleviate that burden. Our dedicated team is committed to safeguarding your digital presence
and guiding you toward the right security measures.
Rely on our tailored solutions, crafted from exhaustive vulnerability assessments and security testing reports, to fortify your online defences effectively.
Explore our comprehensive app security solutions.
From the beginning, the Microsoft SDL identified that security needed to be everyone’s job and included practices in the SDL for program managers, developers, and testers, all aimed at improving security. Further, recognizing that one size doesn’t fit all development approaches, it described flexible practices and activities proven to improve security of software applications at every stage of development using either the classic waterfall or newer agile methodology. However, other than considering the production environment, the SDL didn’t include activities for operations engineers.

Ensure everyone understands security best practices.

Define a minimum-security baseline to include in the DevOps process and pipeline.

Define specific metrics to drive action and support compliance objectives.
Analyze and keep an inventory of third-party components and create a plan to evaluate reported vulnerabilities.

Use threat modeling to identify security vulnerabilities, determine risk, and mitigate.

Carefully select tools and intelligent automation to help engineers and ensure consistency.

Avoid hiding secrets in code, as application code cannot defend itself from an attacker.

Monitor your applications for performance and security issues to help reduce mean time to identify and contain attacks.
Practice #1—Provide Training
Practice #2—Define Requirements
Practice #3—Define Metrics and Compliance Reporting
Drive the behavior you want with the engineers by defining specific metrics which drive action and support compliance objectives.
Practice #4—Use Software Composition Analysis (SCA) and Governance
When selecting third-party components (both commercial and open source), it’s important to understand the impact that a vulnerability in the component could have on the overall security of the system. SCA tools can assist with licensing exposure, provide an accurate inventory of components, and report any vulnerabilities with referenced components. You should also be more selective when using high-risk third-party components and consider performing a more thorough evaluation before using them.
Practice #5—Perform Threat Modeling
Although threat modeling can be challenging in DevOps because of its perceived slowness, it is a critical component of any secure development process. In most situations, applying a structured approach to threat scenarios helps a team more effectively and less expensively identify security vulnerabilities, determine risks from those threats, and then make security feature selections and establish appropriate mitigations. At the very least, threat modeling should be used in environments where there is meaningful security risk.
Practice #6—Use Tools and Automation
Use carefully selected tools and intelligent automation that’s integrated into the engineer’s world (such as an integrated development environment). In the modern engineering world, it’s easy to assume that automation is the solution and it’s correct that automation is critical, but it’s important to be selective when choosing tools and be careful when deploying them. The goal is to fix issues and not to overload engineers with too many tools or alien processes outside of their everyday engineering experience.
![]() Tools must be integrated into the CI/CD pipeline.
Tools must be integrated into the CI/CD pipeline.![]() Tools must not require security expertise.
Tools must not require security expertise.![]() Tools must avoid a high false-positive rate of reporting issues.
Tools must avoid a high false-positive rate of reporting issues.
Integrating Static Application Security Testing (SAST) into your IDE (integrated development environment) can provide deep analytical insight into the syntax, semantics, and provide just-in-time learning, preventing the introduction of security vulnerabilities before the application code is committed to your code repository. Similarly, integrating Dynamic Analysis Security Testing (DAST) tools into the continuous integration / continuous delivery pipeline will help quickly uncover issues only apparent when all components are integrated and running.
Practice #7—Keep Credentials Safe
Scanning for credentials and other sensitive content in source files is necessary during pre-commit as they reduce the risk of propagating the sensitive information into your team’s CI/CD process. Instead of storing sensitive keys in code, consider using a bring-your-own-key (BYOK) solution that generates keys using a hardware security module (HSM).

Ensure everyone understands security best practices.

Define a minimum-security baseline to include in the DevOps process and pipeline.

Define specific metrics to drive action and support compliance objectives.

Analyze and keep an inventory of third-party components and create a plan to evaluate reported vulnerabilities.

Use threat modeling to identify security vulnerabilities, determine risk, and mitigate.

Carefully select tools and intelligent automation to help engineers and ensure consistency.

Avoid hiding secrets in code, as application code cannot defend itself from an attacker.

Monitor your applications for performance and security issues to help reduce mean time to identify and contain attacks.
Practice #1—Provide Training
Practice #2—Define Requirements
Practice #3—Define Metrics and Compliance Reporting
Drive the behavior you want with the engineers by defining specific metrics which drive action and support compliance objectives.
Practice #4—Use Software Composition Analysis (SCA) and Governance
When selecting third-party components (both commercial and open source), it’s important to understand the impact that a vulnerability in the component could have on the overall security of the system. SCA tools can assist with licensing exposure, provide an accurate inventory of components, and report any vulnerabilities with referenced components. You should also be more selective when using high-risk third-party components and consider performing a more thorough evaluation before using them.
Practice #5—Perform Threat Modeling
Although threat modeling can be challenging in DevOps because of its perceived slowness, it is a critical component of any secure development process. In most situations, applying a structured approach to threat scenarios helps a team more effectively and less expensively identify security vulnerabilities, determine risks from those threats, and then make security feature selections and establish appropriate mitigations. At the very least, threat modeling should be used in environments where there is meaningful security risk.
Practice #6—Use Tools and Automation
Use carefully selected tools and intelligent automation that’s integrated into the engineer’s world (such as an integrated development environment). In the modern engineering world, it’s easy to assume that automation is the solution and it’s correct that automation is critical, but it’s important to be selective when choosing tools and be careful when deploying them. The goal is to fix issues and not to overload engineers with too many tools or alien processes outside of their everyday engineering experience.
![]() Tools must be integrated into the CI/CD pipeline.
Tools must be integrated into the CI/CD pipeline.![]() Tools must not require security expertise.
Tools must not require security expertise.![]() Tools must avoid a high false-positive rate of reporting issues.
Tools must avoid a high false-positive rate of reporting issues.
Integrating Static Application Security Testing (SAST) into your IDE (integrated development environment) can provide deep analytical insight into the syntax, semantics, and provide just-in-time learning, preventing the introduction of security vulnerabilities before the application code is committed to your code repository. Similarly, integrating Dynamic Analysis Security Testing (DAST) tools into the continuous integration / continuous delivery pipeline will help quickly uncover issues only apparent when all components are integrated and running.
Practice #7—Keep Credentials Safe
Scanning for credentials and other sensitive content in source files is necessary during pre-commit as they reduce the risk of propagating the sensitive information into your team’s CI/CD process. Instead of storing sensitive keys in code, consider using a bring-your-own-key (BYOK) solution that generates keys using a hardware security module (HSM).

To improve their efficiency, DevSecOps teams typically use open source tools like Terraform to manage and provision infrastructure like networks, virtual machines, and load balancers through code rather than doing it manually. Terraform helps ensure that infrastructure is set up and updated consistently across hundreds or thousands of servers. To reduce the risk that misconfigurations are deployed to the production environment, infrastructure as a code scanning tools automatically check the infrastructure at the code level for noncompliance with security policies and standards.

Before their code is compiled, DevSecOps developers begin testing their custom code for security vulnerabilities. This helps them fix issues without affecting the build. Static application security testing tools make this process easier with automatic checks and real-time feedback. Many tools identify exactly which code is risky and offer suggested fixes.

One way that teams build applications and features more efficiently is by using third-party plug-ins and frameworks. These prebuilt tools save time, but they may also introduce risks, such as issues with the licensing, poorly written code, or security vulnerabilities. Software composition analysis tools identify open source components in applications and evaluate them against proprietary or free databases to detect license violations and security and quality issues.

During quality assurance testing or when an application is being used, interactive application security tools scan the code to find vulnerabilities and provide reports that identify where in the code the issue is.

Dynamic application security testing emulates the methods a bad actor might use to attack an application. This testing occurs while the application is running and is based on predefined use cases.

Containers are widely used in DevSecOps because they help developers easily deploy self-contained units of code. Within a container is a container image that includes the code that runs processes for the container. However, these images are often built using existing images or pulled from public repositories. Container scanning tools, scan containers and compare them against public or proprietary vulnerability databases to uncover potential security issues.

Tailored packages for SMB's to uplift cyber security

Risk-based approach for large enterprises to uplift cyber security

Work Security Beyond Boundaries with Microsoft Surface
Application security involves the processes, tools, and practices aimed at protecting applications from threats throughout their lifecycle. This includes coding practices, penetration testing, and securing application infrastructure to prevent unauthorized access and data breaches.
Application security is crucial to protect sensitive data, maintain user trust, comply with regulations, and avoid financial losses due to breaches and downtime. Effective security measures help in identifying and mitigating vulnerabilities early, reducing the risk of attacks.
Common risks include:
SQL Injection: Exploiting vulnerabilities in an application's database queries.
Cross-Site Scripting (XSS): Injecting malicious scripts into web pages.
Cross-Site Request Forgery (CSRF): Forcing a user to execute unwanted actions.
Insecure Deserialization: Executing malicious code via deserialization of untrusted data.
Security Misconfigurations: Poorly configured security settings.
The OWASP Top 10 is a standard awareness document highlighting the ten most critical web application security risks. It serves as a guide for developers and security professionals to understand and mitigate the most common threats.
A security vulnerability assessment is a systematic review of an application to identify, evaluate, and prioritize security vulnerabilities. It involves scanning and testing the application to uncover potential security flaws and recommend remediation strategies.
DevSecOps is a process that integrates security into the entire software development lifecycle. Organizations adopt this approach to reduce the risk of releasing code with security vulnerabilities. Through collaboration, automation, and clear processes, teams share responsibility for security, rather than leaving it to the end when it can be much more difficult and costly to address issues.
DevSecOps stands for development, security, and operations. It refers to the process of integrating security into all phases of software development.
Shift left is a concept in DevSecOps that refers to incorporating security practices starting from the very beginning of the development process.
The DevSecOps framework includes continuous integration, continuous delivery, and continuous security. It is a method by which security, operations, and security teams work together and share the responsibility for quickly delivering quality software, while reducing security vulnerabilities.
There is no one DevSecOps process, but a common way that people run these projects is by dividing work into sprints each of which includes the following components: planning and development, build and test, and production. Throughout the sprint, teams use automation to continuously address quality assurance issues, continuously integrate, and continuously test for security risks.
Application security testing (AST) involves the process of making applications more secure by identifying and fixing vulnerabilities. It encompasses various methods and tools to ensure applications are protected against threats and attacks.
SAST analyzes source code, bytecode, or binary code for security vulnerabilities without executing the program. It is often integrated into the development process to detect issues early.
DAST tests the application in its running state, simulating attacks to identify vulnerabilities in a live environment. It focuses on identifying issues that can be exploited from outside the application.
IAST combines elements of SAST and DAST by analyzing code in real-time while the application runs. It provides more context-aware results by monitoring the application during testing.
SCA tools analyze the open-source components and libraries used in an application to identify known vulnerabilities, license compliance issues, and outdated components.
Also known as pen testing, this involves simulated attacks by security experts to find and exploit vulnerabilities. It is a manual testing approach that mimics real-world attack scenarios.
Penetration Testing: Simulates an attack on the application to identify security weaknesses that could be exploited by attackers. It often involves manual testing techniques to exploit vulnerabilities.
Vulnerability Assessment: A broader approach that identifies and evaluates vulnerabilities but does not necessarily attempt to exploit them. It focuses on finding and documenting potential issues.

