CISO Online™ stands as a forefront provider of data protection cybersecurity services, offering a holistic approach to fortify your digital assets. Our comprehensive solution encompasses cutting-edge features such as Data Classification and Labelling, ensuring a structured approach to safeguarding sensitive information.
Click to discover how CISO Online™ can empower your organisation with advanced cybersecurity solutions.
The exponential growth of data, blurring of traditional organisational boundaries, and increased workforce collaboration, has made protecting and governing important data more challenging than ever. Data is created, stored, and shared across many locations – devices, apps, cloud services and on-premises. The evolving compliance landscape only adds to the complexity. CISO Online’s comprehensive solutions enable you to protect and govern your data, throughout its lifecycle – wherever it lives, or wherever it travels. We give customers the flexibility to implement the necessary controls to meet both internal and external security and compliance requirements.
We employ state-of-the-art Data Loss Prevention (DLP) measures, proactively identifying and mitigating potential data breaches. What sets us apart is our seamless Integration of Data Classification and DLP, creating a robust defence against evolving cyber threats.

The first challenge many organisations face is identifying what kind of,
and how much, data exists in their environment. You need a deep
understanding of how much sensitive data exists and where it is stored before it can be protected and governed. This information is critical to assess your overall risk, which helps you define your strategy for protecting and governing the data. Start your journey by discovering and classifying important data across your environment.
Here are some of the types of questions you will answer during this process:
CISO Online™ seamlessly integrates Data Classification and DLP to bring forth a synergy that enhances your organisation’s overall cybersecurity posture. This integration ensures that data classification informs DLP policies, aligning the security measures precisely with the sensitivity of the data. Additionally, automated responses based on data classification streamline incident response, mitigating potential risks promptly and effectively. Through user awareness programs, we educate employees about the importance of data classification, fostering a culture of awareness and responsibility regarding data protection
Contact us today to fortify your data against evolving cyber threats. Your security is our priority
In today’s digital landscape, safeguarding data protection is paramount for organisations navigating the complexities of cybersecurity. Neglecting this crucial aspect exposes businesses to a myriad of threats, including identity theft and fraud, which can have far-reaching consequences. Such oversights not only put sensitive data at risk but also undermine trust, compromise competitive advantages, and threaten the very foundation of success in an interconnected global marketplace.
Beyond simply mitigating cyber threats, our mission extends to cultivating a culture of cybersecurity awareness within organisations. By instilling a proactive mindset and fostering best practices, we empower businesses to navigate the ever-evolving cyber risks landscape with resilience. This proactive approach not only enhances operational security but also safeguards reputation, a priceless asset in today’s interconnected world.
Choosing to partner with CISO Online™ signifies a dedication to upholding the security and integrity of your business in the face of intricate digital challenges. Our tailored solutions and comprehensive approach ensure that you remain shielded from the rising tide of cyber threats, offering peace of mind in an era where data protection is paramount.
Cyber safety starts here. ensure your organisation is protected against the growing threats of data breaches and cybercrime in today’s digital era.
Are you a business owner, organisation, or government entity grappling with the complexities of data security solutions?
CISO Online™ is here to alleviate your concerns and provide clarity.
Our mission is to safeguard your data and guide your business towards optimal security measures. We achieve this by delivering customised solutions, let’s explore these…
Here are our key solutions for your data protection needs
Unlock Unmatched Data Protection with CISO Online's Integration of Microsoft Purview
Glossary with business and technical search terms to aid data discovery
Unified map of your data assets and their relationships for more effective data governance
In-place data sharing in near real time and easy provisioning of data access
Insights into the management of sensitive data across your entire data estate
At CISO Online™, we understand that data is the lifeblood of modern organisations. Protecting and harnessing this valuable asset requires robust data governance, classification, and labelling. That’s why we’ve partnered with Microsoft to bring you an integrated solution that empowers your data management strategy: Microsoft Purview.

Fortify your Data with Microsoft Defender for Endpoint

industry regulations. End users don’t always know what information
industry regulations. End users don’t always know what information they’re permitted to share with others in and outside the organization. They may also share sensitive data accidentally. The data loss prevention (DLP) solution detects sensitive content and helps prevent accidental oversharing in and outside the organisation.
Let’s delve into how this partnership benefits your data security strategy:
1. Seamless Onboarding with Defender for Endpoint
2. Centralised Control and Behavior Management
3. Advanced Classification and Protection
4. Data Lineage and Governance
Enhance security with industry- leading Al and automation
Protect against advanced cyberattacks with XDR
Strengthen email security without compromise
Get comprehensive security for collaboration tools
Key Features:
1. Native Email Security
2. Comprehensive Collaboration Tool Security
3. Industry-Leading AI and Automation
4. Advanced Cyberattack Protection with XDR
Elevate Your Data Protection with CISO Online's Cloud Protection
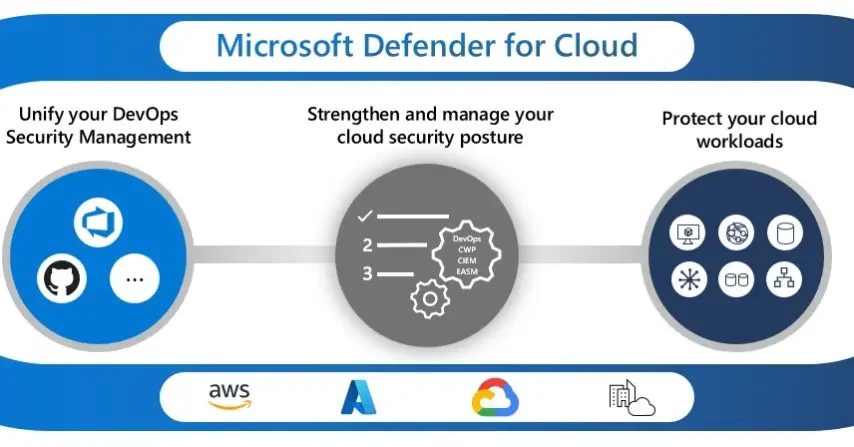
At CISO Online™, we understand the critical importance of safeguarding your organisation’s sensitive data in the cloud. As cyber threats continue to evolve, robust data loss prevention (DLP) measures are essential to prevent accidental or malicious data leaks. That’s why we’ve partnered with Microsoft to offer a comprehensive solution that combines the power of Cloud DLP with Microsoft Defender for Cloud.
Reduce risk with contextual security posture management
Help prevent, detect, and respond quickly to cyberthreats

Unify security management fo DevOps
Securing Your Cloud Applications with Microsoft Defender for Cloud
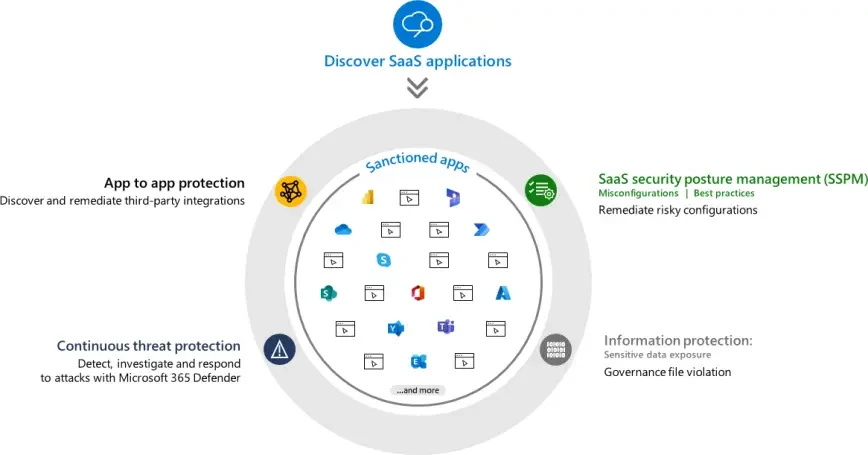
In today’s hybrid work environments, Software as a Service (SaaS) applications are the backbone of productivity. However, protecting these apps and the critical data they house presents a formidable challenge for organisations. As employees access company resources beyond the corporate perimeter, new attack vectors emerge. At CISO Online™, we recognise the urgency of safeguarding your cloud app data, and that’s why we’ve partnered with Microsoft to introduce Microsoft Defender for Cloud Apps.
The SaaS Security landscape today results in SaaS apps being everywhere—driving collaboration, communication, and business processes. But their widespread adoption also exposes organisations to risks. Beyond traditional Cloud Access Security Brokers (CASBs) provide valuable insights, but they fall short in addressing the full spectrum of SaaS security challenges. We need a more comprehensive approach.
1. Fundamental CASB Functionality
2. SaaS Security Posture Management (SSPM)
3. Advanced Threat Protection
4. App-to-App Protection
Connect with our skilled cybersecurity team to fortify your organisation against cyber threats and ensure robust protection for your identity, data, and digital assets. Learn how CISO Online™ utilises these strategies to safeguard your organisation’s digital landscape today!

Tailored packages for SMB's to uplift cyber security

Risk-based approach for large enterprises to uplift cyber security

Work Security Beyond Boundaries with Microsoft Surface
Data protection involves safeguarding important information from corruption, compromise, or loss. It encompasses policies, procedures, and technologies that ensure data privacy and security.
Data protection is crucial for maintaining the privacy of individuals, protecting sensitive information, complying with regulations, and ensuring business continuity.
Common methods include encryption, access control, data masking, backup and recovery, data loss prevention (DLP), and secure data disposal.
Data encryption is the process of converting plaintext data into a coded form (ciphertext) to prevent unauthorized access. It requires a key for decryption to read the original data.
Data privacy focuses on managing how data is collected, used, and shared, ensuring that individuals’ information is handled according to their preferences. Data security focuses on protecting data from unauthorized access and breaches.
Major regulations include the General Data Protection Regulation (GDPR), California Consumer Privacy Act (CCPA), Health Insurance Portability and Accountability Act (HIPAA), and the Sarbanes-Oxley Act (SOX).
The GDPR is a regulation in the European Union that sets guidelines for the collection and processing of personal data. It mandates stringent data protection measures and grants individuals rights over their personal data.
Data masking involves obscuring specific data within a database to protect it from unauthorized access while maintaining its usability for testing and analysis. It’s often used to protect sensitive information.
Organizations can ensure data protection in the cloud by using encryption, implementing access controls, regularly auditing and monitoring cloud services, and choosing reputable cloud providers.
A data breach is an incident where sensitive, protected, or confidential data is accessed or disclosed without authorization. Steps include identifying and containing the breach, assessing the impact, notifying affected parties, and improving security measures.
Microsoft DLP is a set of tools and features integrated into Microsoft 365 services designed to identify, monitor, and protect sensitive information across emails, documents, and other data stored in cloud services.
Microsoft DLP can detect a wide range of sensitive information types, including credit card numbers, Social Security numbers, health records, financial data, and custom sensitive information defined by the organization.
Microsoft DLP uses content analysis techniques, such as pattern matching and machine learning, to identify sensitive information. It then applies policies to control how this information is shared and handled.
Microsoft DLP is supported across several Microsoft 365 services, including Exchange Online, SharePoint Online, OneDrive for Business, Microsoft Teams, and Microsoft Endpoint Manager.
Actions include notifying users, blocking content from being shared, logging the event, encrypting the email, and allowing users to override the policy with justification.
Yes, DLP policies can be customized to match the specific needs of an organization. You can define custom sensitive information types, set specific conditions, and choose appropriate actions.
Microsoft DLP provides default templates for various regulatory and industry standards, including GDPR, HIPAA, PCI-DSS, and more, to help organizations quickly implement compliance measures.
DLP reports and alerts provide visibility into policy enforcement, help identify potential data breaches, and allow administrators to take corrective actions.
In Exchange Online, DLP scans emails and attachments for sensitive information and applies policies to prevent unauthorized sharing, such as blocking the email or encrypting its contents.
Yes, DLP policies can monitor and protect documents stored in SharePoint Online and OneDrive for Business by identifying sensitive content and restricting access or sharing based on policy rules.
Endpoint DLP extends data protection to endpoints (like laptops and desktops) by monitoring and controlling actions such as copying sensitive data to USB drives or uploading it to unapproved cloud services.
Organizations can use Microsoft DLP to implement and enforce policies that align with regulatory requirements, monitor compliance, and generate reports for audits.
Microsoft DLP allows fine-tuning of policies and the use of conditions and exceptions to reduce false positives. Administrators can review incidents and adjust policies as needed.
Yes, DLP policies can be tested in audit mode, where they monitor and report policy matches without enforcing actions, allowing administrators to refine policies before full deployment.
DLP policies should be regularly reviewed and updated to address evolving threats, changing business needs, and new regulatory requirements. This includes refining detection rules, updating actions, and ensuring policies remain effective.
Microsoft DLP refers to a set of technologies and strategies designed to prevent the unauthorized disclosure, leakage, or loss of sensitive data. It helps protect sensitive information from accidental or intentional exposure across various locations such as Exchange Email, SharePoint sites, OneDrive accounts, Teams chat and channel messages, Endpoint Devices, Cloud Apps, and on-premises repositories.
Microsoft Purview is leveraged to define DLP policies safeguarding data across multiple locations. It works in conjunction with AAD, Endpoint DLP, Defender for Endpoint, and Defender for Cloud capabilities to detect and prevent exfiltration of sensitive and protected data from endpoint devices.
Key features include the ability to identify and classify sensitive information, define policies to control access to sensitive information, and track the movement of sensitive information within the organization to prevent unauthorized access and data breaches
Endpoint DLP supports Windows 10 Enterprise 1809+ and the three latest released versions of macOS. There is an evaluation for expanding support for Linux and mobile platforms in the future.
For Windows devices, Microsoft Edge, Google Chrome (with Microsoft Purview Chrome Extension), and Firefox (coming soon) are supported for blocking the upload of sensitive files to cloud apps. For macOS devices, Safari is also supported.
Microsoft Defender for Cloud helps prevent, detect, and respond to threats with increased visibility into and control over the security of your resources. It provides integrated security monitoring and policy management across your subscriptions and works with a broad ecosystem of security solutions.
Microsoft Defender for Cloud Apps is a feature that provides expanded visibility and control over apps that access your Microsoft 365 data. It tracks non-Microsoft apps that use OAuth to authenticate to Microsoft Entra ID, as well as Google and Salesforce, and provides out-of-box detections and customizable policies that track various app attributes and behaviors.
Microsoft Defender for Cloud Apps can generate alerts based on Microsoft threat intelligence to identify apps that are malicious and track various app attributes and behaviors that can indicate misuse and risk.

