Trust CISO Online™ for unparalleled expertise and top-tier cybersecurity solutions!

In today’s digital landscape, neglecting cybersecurity, particularly in endpoint protection, exposes businesses to a myriad of risks, including data breaches, financial losses, reputational damage, operational disruptions, and legal consequences. Our team at CISO Online™ has meticulously aligned our solutions with leading technology firms to fortify your organisation’s and customers’ digital assets
comprehensively. As cybersecurity experts, we understand the intricacies of digital threats and the paramount importance of robust endpoint protection strategies.
Endpoint protection is more than just safeguarding devices; it’s about creating a secure environment where every endpoint is defended and monitored. This includes implementing advanced threat detection methods, endpoint security protocols, and continuous monitoring of network activities to detect and mitigate potential threats promptly.

By focusing on these areas, we aim to not only defend against attacks butalso to build a culture of security awareness within your organisation, ensuring that your operations remain resilient in the face of evolving cyber threats.
CISO Online™ provides a comprehensive suite of services, serving as your strategic partner in the battle against cyber threats. Elevate your organization’s cybersecurity posture and ensure a worry-free digital experience by clicking to fortify your endpoints. Invest in comprehensive cybersecurity strategies for endpoint protection to safeguard valuable assets, maintain business continuity, and fortify overall resilience against evolving cyber threats.
Contact us today to fortify your data against evolving cyber threats. Your security is our priority.

In the realm of cybersecurity, safeguarding endpoint devices is critical to protecting sensitive data and mitigating cyber threats. Neglecting to fortify these endpoints exposes organisations to a myriad of risks, including data breaches and malware attacks, which can have devastating consequences. Such oversights not only compromise the security of valuable assets but also erode trust, diminish competitive advantages, and jeopardise the very foundation of success in today’s digitally driven landscape.
At CISO Online™, we are dedicated to addressing the pressing need for advanced endpoint protection solutions tailored to the specific demands of the contemporary digital environment. Our focus lies in developing robust defences against malware, ransomware, and other cyber threats, ensuring the ongoing safety of endpoint devices and preserving the integrity of organisational networks.
Beyond simply mitigating cyber threats, our mission extends to fostering a culture of cybersecurity awareness within organisations. By instilling a proactive mindset and promoting best practices for endpoint security, we empower businesses to navigate the ever-evolving landscape of cyber risks with resilience. This proactive approach not only enhances operational security but also safeguards reputation, a priceless asset in today’s interconnected world.
Choosing to partner with CISO Online™ signifies a commitment to upholding the security and integrity of your organisation’s endpoint devices. Our tailored solutions and comprehensive approach ensure that you remain protected against the growing threats of malware infections, data breaches, and cyber attacks. With CISO Online™ by your side, you can rest assured that your endpoints are shielded from harm, offering peace of mind in an era where endpoint protection is paramount.
Struggling to navigate the vast array of endpoint protection solutions available? At CISO Online™, we specialise in alleviating the confusion and uncertainty surrounding your cybersecurity needs.
Our tailored approach ensures your business is shielded from threats with precision, driven by meticulous vulnerability assessments. Explore our bespoke solutions designed to fortify your endpoints and safeguard your digital assets.
Here are our key solutions for your endpoint protection needs.
Automated investigation and remediation
Attacksurface
reduction
Core Defender Vulnerability Management
Endpoint detection and response
Automated investigation and remediation
Attacksurface
reduction
Automated investigation and remediation
Endpoint detection and response
In today’s digital landscape, protecting your endpoints from advanced cyber threats is paramount to safeguarding your organisation’s sensitive data and maintaining
operational continuity. That’s why CISO Online™ is proud to leverage the cutting-edge
capabilities of Microsoft Defender for Endpoint to offer comprehensive endpoint protection solutions to our valued customers.
Defender for Endpoint utilises a combination of technology, including:
![]() Endpoint Behavioural Sensors
Endpoint Behavioural Sensors
![]() Cloud Security Analytics
Cloud Security Analytics
![]() Threat Intelligence
Threat Intelligence
CISO Online™ is committed to providing cutting-edge endpoint protection solutions to our valued customers, leveraging a combination of advanced technologies including Antivirus (AV), Host-Based Firewall (HFW), Host Intrusion Prevention System (HIPS), Extended detection and response (XDR), HFW, and Endpoint Detection and Response (EDR).
Our endpoint protection solutions are designed to detect and respond to threats in real-time, helping organisations stay one step ahead of cybercriminals.
Choose CISO Online™ today and harness the power of Microsoft Defender for Endpoint to strengthen your organisation’s cybersecurity defences.
In today’s digital landscape, protecting your endpoints from advanced cyber threats is paramount to safeguarding your organisation’s sensitive data and maintaining
operational continuity. That’s why CISO Online™ is proud to leverage the cutting-edge
capabilities of Microsoft Defender for Endpoint to offer comprehensive endpoint protection solutions to our valued customers.
Defender for Endpoint utilises a combination of technology, including:
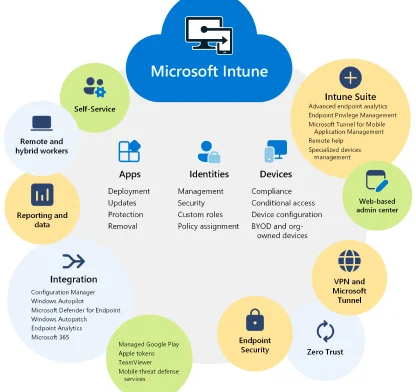

Safeguarding Your Endpoints with CISO Online™ and Microsoft Intune
Using Microsoft Intune, a cloud-based endpoint management solution, simplifies app and device management across various devices, including mobile devices, desktop computers, and virtual endpoints.
We manage user access to organisational resources efficiently with Intune to simplify the process of managing different devices that access organisation resources, ensuring seamless collaboration and secure access, regardless of their location.
Microsoft Intune simplifies endpoint management through the following strategies:
1. Comprehensive Device Management
![]() Including Mobile devices, Desktop computers and Virtual endpoints
Including Mobile devices, Desktop computers and Virtual endpoints
2. Efficient App Management
![]() Simplified app distribution
Simplified app distribution
![]() Enforce app’s security policies
Enforce app’s security policies
3. User Access Management
![]() Enables seamless collaboration
Enables seamless collaboration
![]() Policies established for conditional access
Policies established for conditional access
4. Elevate Your Endpoint Protection Strategy
![]() Seamlessly integrate with other Microsoft solutions
Seamlessly integrate with other Microsoft solutions
![]() Automated compliance checks
Automated compliance checks
When you choose CISO Online™, you’re not just getting a solution; you’re gaining a strategic ally committed to your organisation’s security. Elevate your endpoint protection strategy with Microsoft Intune. Contact us today to fortify your defences safeguard your digital assets.
Engaging with our expert cybersecurity team will not only protect your organisation against cyber threats but also ensure robust identity protection, safeguarding your data and digital assets from unauthorised access and breaches. Discover how CISO Online™ leverages the above strategies to secure your identity and digital assets today!

Tailored packages for SMB's to uplift cyber security

Risk-based approach for large enterprises to uplift cyber security

Work Security Beyond Boundaries with Microsoft Surface
Microsoft Defender for Endpoint is an endpoint security platform that helps protect devices running Windows, macOS, Linux, and mobile operating systems against advanced threats.
Endpoint Detection and Response (EDR): Detects and investigates advanced attacks and suspicious activities across endpoints.
Next-Generation Antivirus (NGAV): Uses machine learning and behavioral analysis to protect against known and unknown threats.
Endpoint Protection: Prevents malware infections and other threats by enforcing security policies on endpoints.
Automated Investigation and Response: Provides automated responses to detected threats to reduce the impact of security incidents.
Yes, Microsoft Defender for Endpoint includes antivirus capabilities (NGAV) along with advanced threat protection features, aiming to provide comprehensive endpoint security.
It integrates with Microsoft 365 security services, Azure Security Center, and other Microsoft Defender products (like Microsoft Defender for Office 365) to provide a unified security management experience.
It uses behavioral analysis, machine learning, and cloud-delivered protection to detect and respond to these types of threats in real-time.
Yes, it can be managed centrally through the Microsoft Defender Security Center or through Microsoft Endpoint Manager for integrated management of endpoints and security.
Yes, it adheres to various compliance standards and regulations, such as GDPR, HIPAA, and others, helping organizations meet their regulatory requirements.
You can find detailed documentation, guides, and support resources on the official Microsoft Defender for Endpoint webpage, as well as through Microsoft's technical support channels and community forums.
Microsoft Intune is a cloud-based service that focuses on mobile device management (MDM) and mobile application management (MAM). It helps organizations manage the devices employees use to access company data and applications.
Intune can manage a variety of devices, including Windows PCs, macOS computers, iOS/iPadOS devices, and Android devices.
Intune integrates with Azure Active Directory (Azure AD) for identity and access management, Azure Information Protection for data protection, and Office 365 for application management. It is also part of the Microsoft Endpoint Manager suite, which combines Intune and System Center Configuration Manager (SCCM).
Device management, application management, policy enforcement, compliance reporting, conditional access, and support for BYOD (Bring Your Own Device) scenarios are some of the main features.
Intune helps enforce security policies on devices, manage device compliance, and ensure that only compliant devices can access corporate resources. It also supports encryption, password policies, and remote wipe capabilities.
Conditional access policies are used to control access to corporate resources based on specific conditions such as device compliance status, user location, and application sensitivity.
MDM (Mobile Device Management) focuses on managing the entire device, including settings, apps, and data. MAM (Mobile Application Management) focuses on managing and protecting specific applications and their data without necessarily managing the entire device.
Yes, Intune can manage devices that are not joined to a traditional on-premises Active Directory domain. Devices can be enrolled through Azure AD join or as personal devices (BYOD).
Intune is available through various licensing options, including Microsoft 365 E3/E5, Enterprise Mobility + Security (EMS) E3/E5, and as a standalone service. Licensing details can vary, so it's important to check the specific requirements based on your organization's needs.
Intune supports BYOD by allowing employees to enroll their personal devices in a way that gives them access to corporate resources while keeping personal data separate and private.
The Company Portal is an app that users install on their devices to enroll in Intune, access corporate resources, install apps, and receive support from their IT department.
Yes, Intune is well-suited for remote work scenarios by allowing IT administrators to manage and secure devices regardless of their location, ensuring that employees can access necessary resources securely from anywhere.
Intune provides capabilities to manage software updates for Windows, macOS, iOS, and Android devices. Administrators can configure update rings, deployment schedules, and compliance policies to ensure devices are up to date.
Intune offers various reports and dashboards that provide insights into device compliance, app deployment status, user activity, and overall device health. These reports help administrators monitor and manage their device fleet effectively.

