Elevate your online security posture and stay ahead of evolving threats today!

In today’s digital landscape, neglecting cyber security, particularly in identity protection, exposes businesses to a myriad of risks, including data breaches, financial losses, reputational damage, operational disruptions, and legal consequences.
Our team at CISO Online™ has meticulously aligned our solutions with leading technology firms to fortify your organisation’s and customers’ digital assets comprehensively. As cybersecurity experts, we understand the intricacies of digital threats and the paramount importance of robust identity protection strategies.

Identity protection is more than just safeguarding passwords; it’s about creating a secure environment where every transaction and interaction is verified and protected. This includes implementing advanced encryption methods, multi-factor authentication, and continuous monitoring of digital footprints to detect and mitigate potential threats promptly. By focusing on these areas, we aim to not only defend against attacks but also to build a culture of security awareness within your organisation, ensuring that your operations remain resilient in the face of evolving cyber threats.
CISO Online™ is a cybersecurity company dedicated to safeguarding digital identities across various sectors, including government bodies and businesses ranging from small to mid-sized enterprises. If your organisation falls within these categories, you have come to the right place.
Contact us today to fortify your data against evolving cyber threats. Your security is our priority.


Contact us today to fortify your data against evolving cyber threats. Your security is our priority.
In the digital age, neglecting cybersecurity, particularly identity protection, exposes organisations to numerous threats. Ignoring the need for comprehensive cybersecurity not only risks sensitive data but also erodes trust, diminishes competitive edge, and jeopardies the foundational pillars of success in a globally connected marketplace.
CISO Online™ is dedicated to providing advanced cybersecurity solutions tailored to the specific demands of the contemporary digital environment. We’re here to help you develop a robust defence against identity theft and fraud, ensuring the ongoing safety of your digital identity and preserving the trust of your customers and partners.
Are you a business owner, organisation, or government entity feeling overwhelmed, uncertain about which identity protection solutions and products best suit your needs? At CISO Online™, we’re committed to easing that burden for you.
We aim to protect and steer your business in the right direction by providing tailored solutions based on comprehensive vulnerability and security testing reports.
Here are our key solutions for your identity security needs.
Safeguard Your Digital Identity with CISO Online’s Microsoft Azure Identity Protection Services
Partnering with Microsoft, CISO Online™ brings you the first of the Solutions implemented to ensure Identity Protection. Identity Access Management (IAM), as well as a dedicated Identity Provider (IDP).

IAM: Identity and Access Management is a framework of policies, processes, and technologies that ensures the right individuals have the right access to the right resources at the right time and for the right reasons.
IDP: An Identity Provider (IDP) is a system or service that manages and verifies digital identities. IDPs are responsible for authenticating users, providing them with access to resources based on their identity, and managing the permissions and attributes associated with their identity.
These Identity Protection Services, powered by Microsoft Entra (Azure?), adopt a multi-layered approach to defend against malicious login attempts and safeguard your credentials. We prioritise risk-based access controls, identity protection tools, and strong authentication options, ensuring the resilience of your online presence. Our expert team ensures seamless integration of Microsoft Entra into your existing systems. And with this integration we can guarantee a swift and effective deployment of Identity Protection measures across your organisation, without disrupting your day-to-day operations.

Strengthen Your Digital Fortress with MFA
![]() MFA: Multi-factor authentication (MFA) is a security process that requires users to provide two or more verification factors to gain access to a resource, such as an application, online account, or network. This additional layer of security helps protect against unauthorized access by requiring something the user knows (password), something the user has (security token or smartphone), or something the user is (biometric verification) to verify their identity.
MFA: Multi-factor authentication (MFA) is a security process that requires users to provide two or more verification factors to gain access to a resource, such as an application, online account, or network. This additional layer of security helps protect against unauthorized access by requiring something the user knows (password), something the user has (security token or smartphone), or something the user is (biometric verification) to verify their identity.
CISO Online™ provides these services with Microsoft Azure, and seamlessly integrate MFA into your existing authentication processes, ensuring a robust defence against cyber threats.
Our expert team ensures that MFA becomes a natural and user-friendly part of your digital identity protection strategy. Whether it’s through multiple devices, one-time passwords, or other authentication factors, we tailor MFA solutions to meet your unique needs.
In collaboration with Microsoft, CISO Online™offers advanced Single Sign-On (SSO) services as our third entry for Identity Protection.
![]() SSO: Single Sign-On (SSO)
SSO: Single Sign-On (SSO)
is a user authentication process that allows a user to access multiple applications or services with a single set of login credentials (such as username and password). With SSO, users do not have to enter their credentials separately for each application, which enhances user experience and productivity.
With some of the key features of Microsoft Entra’s SSO solution including:

Increased employee productivity: Simplify access and app discovery with a centralised app-launching experience.
Enhanced security: Minimise the risk of breaches by reducing the reuse of usernames and passwords across apps.
Increased IT efficiency: Centralise user account management and automate user access based on group membership or roles.
With our SSO solution powered by Microsoft Entra ID, users can seamlessly access their SaaS applications with a single set of login credentials, regardless of their location or device.
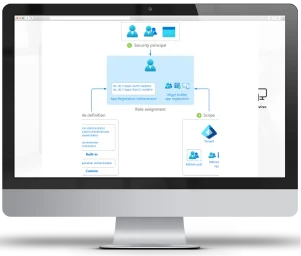

Empower Your Digital Identity with Role-Based Access Control
![]() RBAC: Role-Based Access Control (RBAC) is a method of restricting network access based on the roles of individual users within an organization. In RBAC, permissions are assigned to roles, and users are assigned to appropriate roles. This ensures that users have access only to the resources and information necessary for their roles, reducing the risk of unauthorized access.
RBAC: Role-Based Access Control (RBAC) is a method of restricting network access based on the roles of individual users within an organization. In RBAC, permissions are assigned to roles, and users are assigned to appropriate roles. This ensures that users have access only to the resources and information necessary for their roles, reducing the risk of unauthorized access.
With the key features of our RBAC solutions including:
![]() Simplified access management: Grant access to users based on their roles, ensuring they have the necessary permissions to perform their tasks effectively.
Simplified access management: Grant access to users based on their roles, ensuring they have the necessary permissions to perform their tasks effectively.![]() Reduced risk of unauthorised access: By implementing RBAC, organisations can minimise the risk of unauthorised access and potential security breaches.
Reduced risk of unauthorised access: By implementing RBAC, organisations can minimise the risk of unauthorised access and potential security breaches.![]() Error-resistant identity protection: RBAC minimises errors associated with access control, enhancing resilience and ensuring a robust identity protection solution.
Error-resistant identity protection: RBAC minimises errors associated with access control, enhancing resilience and ensuring a robust identity protection solution.
Our partnership with Microsoft ensures seamless integration and efficient deployment of RBAC solutions, strengthening security posture, while maintaining operational efficiency.
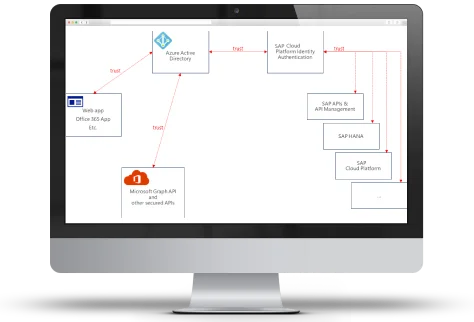
The AAA framework, standing for Authentication, Authorisation, and Accounting, is a comprehensive security framework used in network and system administration. In collaboration with Microsoft, CISO Online™ offers the robust Identity Protections listed above to ensure all three components of the AAA framework are adhered to:

![]() Authentication: Authentication is the process of verifying the identity of a user or system. This typically involves the user providing credentials, such as a username and password, which are then verified by the system. Other authentication factors, such as biometric data or security tokens, may also be used.
Authentication: Authentication is the process of verifying the identity of a user or system. This typically involves the user providing credentials, such as a username and password, which are then verified by the system. Other authentication factors, such as biometric data or security tokens, may also be used.
![]() Authorisation: Authorization is the process of determining what actions a user is allowed to perform within a system. Once a user’s identity has been authenticated, the system checks the user’s permissions to determine whether they are authorized to perform the requested action.
Authorisation: Authorization is the process of determining what actions a user is allowed to perform within a system. Once a user’s identity has been authenticated, the system checks the user’s permissions to determine whether they are authorized to perform the requested action.
![]() Accounting: Accounting involves tracking and recording user activities within a system. This includes logging login and logout events, as well as recording the actions taken by users while they are logged in. Accounting data is often used for auditing and billing purposes.
Accounting: Accounting involves tracking and recording user activities within a system. This includes logging login and logout events, as well as recording the actions taken by users while they are logged in. Accounting data is often used for auditing and billing purposes.

The Least Privilege principle is a security concept that states, users should only be given the minimum level of access or permissions necessary to perform their job functions. CISO Online™, in collaboration with Microsoft, delivers the Solutions listed above to ensure this robust principle is backing up our Identity Protection. The Key aspects of the Least Privilege principle include:
![]() Access Restriction: Users are granted access only to the resources and information required to perform their specific tasks. Access to sensitive or critical resources is restricted to only those users who need it.
Access Restriction: Users are granted access only to the resources and information required to perform their specific tasks. Access to sensitive or critical resources is restricted to only those users who need it.
![]() Role-Based Access Control: RBAC is often used to implement the Least Privilege principle by assigning users to roles based on their job functions.
Role-Based Access Control: RBAC is often used to implement the Least Privilege principle by assigning users to roles based on their job functions.
![]() Privilege Escalation: Users should not have the ability to escalate their privileges beyond what is necessary for their job functions. This helps prevent users from gaining unauthorized access to sensitive information or resources.
Privilege Escalation: Users should not have the ability to escalate their privileges beyond what is necessary for their job functions. This helps prevent users from gaining unauthorized access to sensitive information or resources.
Our approach with Microsoft Entra ID strikes a delicate balance between security and productivity, ensuring that users possess the requisite access levels to fulfill their responsibilities effectively without exposing the organisation to unnecessary risks

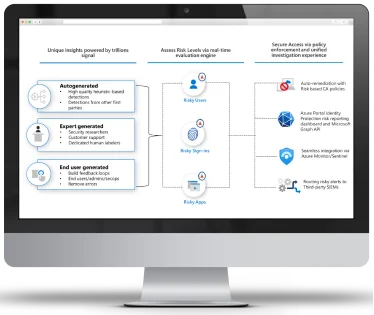
Take advantage of adaptive identity and network access controls to secure access to any app or resource for every user or digital workload across your entire environment.

Implement consistent security policies for every user—employees, frontline workers, customers, partners—as well as apps, devices, and workloads across multicloud and hybrid.

Discover and right-size permissions, manage access lifecycles, and ensure least privilege access for any identity.

Reduce IT friction and improve the hybrid workforce experience with seamless access to any resource, single sign-on, user self-service management, and automated lifecycle workflows

Protect access to resources and data using strong authentication and risk-based adaptive access policies without compromising user experience.

Provide a fast, easy sign-in experience across your multicloud environment to keep your users productive, reduce time managing passwords, and increase productivity.

Manage all your identities and access to all your applications in a central location, whether they’re in the cloud or on-premises, to improve visibility and control.

Take advantage of adaptive identity and network access controls to secure access to any app or resource for every user or digital workload across your entire environment.

Implement consistent security policies for every user—employees, frontline workers, customers, partners—as well as apps, devices, and workloads across multicloud and hybrid.

Discover and right-size permissions, manage access lifecycles, and ensure least privilege access for any identity.

Reduce IT friction and improve the hybrid workforce experience with seamless access to any resource, single sign-on, user self-service management, and automated lifecycle workflows

Protect access to resources and data using strong authentication and risk-based adaptive access policies without compromising user experience.

Provide a fast, easy sign-in experience across your multicloud environment to keep your users productive, reduce time managing passwords, and increase productivity.

Manage all your identities and access to all your applications in a central location, whether they’re in the cloud or on-premises, to improve visibility and control.
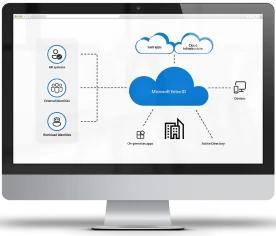
Microsoft Entra ID provides you with common identity and access capabilities across various web services with Microsoft Entra ID. Whether you're utilizing Microsoft 365, Power Platform, Dynamics 365, or other Microsoft products, Microsoft Entra ID seamlessly enables single sign-on and access management for all cloud services.
User accounts configured for Microsoft services are automatically designated within one or more Microsoft Entra ID instances, granting them access to Microsoft Entra ID.
The Microsoft Entra admin center provides a unified view and administration of Microsoft Entra identity and network access solutions. It can be accessed at the official Microsoft Entra website.
The default configuration for user sign-in frequency in Microsoft Entra ID is a rolling window of 90 days. This means users will be asked to sign in again when attempting to access a resource after this period.

