CISO Online™ is at the forefront of cybersecurity, offering advanced Zero Trust solutions to fortify your digital defences.
Embrace a proactive security approach with our comprehensive services, seamlessly integrating the principles of Zero Trust.
Invest in our innovative Zero Trust solutions to stay steps ahead of evolving cyber threats, fostering trust in your digital operations.
At CISO Online™, we rigorously verify every user, device, and network interaction, safeguarding against potential breaches and unauthorised access. Embrace the security of Zero Trust and fortify your digital landscape with CISO Online’s expertise for a worry-free digital future.
Disregarding cybersecurity measures for a Zero Trust model exposes businesses to profound risks, including heightened vulnerability to insider threats, unauthorised access, and potential lateral movement by attackers. The consequences extend from compromised data security and regulatory non-compliance to financial losses and reputational damage.
Without robust protection measures, companies face the grim reality of advanced persistent threats, compromised business processes, and potential data breaches. Proactively investing in comprehensive cybersecurity strategies for a Zero Trust framework is not just a strategic choice but a critical imperative.
The benefits of Zero Trust are clear:
Secure your digital future with zero trust
solutions from CISO Online™ today.


In the realm of cybersecurity, embracing the principles of zero trust is paramount for safeguarding sensitive data and mitigating cyber threats. Neglecting to adopt a zero-trust approach exposes organisations to various risks, including insider threats, lateral movement attacks, and unauthorised access, all of which can have severe consequences. Such oversights not only compromise data integrity but also erode trust, diminish competitive advantages, and jeopardise the foundation of success in today’s interconnected digital landscape.
Why Zero Trust Now?
1. Rapid Digital Adoption Requires Agile Security
The swift integration of digital services demands a security approach that matches its agility.
2. Hyperconnectivity Challenges Cyber Resilience
In an interconnected world, a single security breach can challenge the cyber resilience of the entire organization.
3. The "Assume Trust" Model is Obsolete
Business transformation renders the “assume trust” security model outdated and ineffective.
At CISO Online, our primary focus is on implementing robust security measures that validate every user and device attempting to connect to the network, regardless of their location or status.
Beyond merely mitigating cyber risks, our mission extends to fostering a culture of zero trust within organisations. By instilling a proactive mindset and advocating for best practices in zero trust security, we empower businesses to navigate the ever-evolving cyber landscape with resilience.
This proactive approach not only bolsters operational security but also enhances brand reputation and customer trust, critical assets in today’s competitive market.
With CISO Online as your trusted partner, you can be confident that your zero trust measures are robust, offering peace of mind in an era where security is paramount.
cyber safety begins here. ensure your organisation's zero trust security is shielded against the evolving threat landscape in today's digital age.
Are you a business owner, organisation, or government entity grappling with the complexities of implementing a zero trust security model? Look no further than CISO Online™. We're dedicated to simplifying your journey and ensuring optimal security solutions tailored to your needs. Trust us to steer your business in the right direction.
Always authenticate and authorize based on all available data points, including user identity, location, device health, service or workload, data classification, and anomalies.
Limit user access with just-in-time and just-enough access (JIT/JEA), risk-based adaptive polices, and data protection to help secure both data and productivity.
Minimize blast radius and segment access. Verify end-to-end encryption and use analytics to get visibility, drive threat detection, and improve defenses.
In today’s rapidly evolving digital landscape, traditional security models no longer suffice. That’s why CISO Online™ offers cutting-edge Zero Trust solutions tailored to the needs of modern organisations.
The Zero Trust model revolutionises cybersecurity by assuming breach and verifying each request as though it originates from an open network. Instead of relying on the corporate firewall for protection, Zero Trust adopts a “never trust, always verify” approach to security. Every access request undergoes rigorous authentication, authorisation, and encryption before granting access, regardless of its origin or the resource it seeks to access.
At CISO Online™, we implement Zero Trust principles to safeguard your organisation’s people, devices, apps, and data wherever they’re located. Our solutions incorporate micro-segmentation and least-privilege access principles to minimise lateral movement and bolster security. Additionally, we leverage rich intelligence and analytics to detect and respond to anomalies in real-time, ensuring proactive protection against evolving threats.
Trust CISO Online™ as your partner in Zero Trust security. With our expertise and innovative solutions, you can rest assured that your digital landscape is fortified against cyber threats, today and in the future.
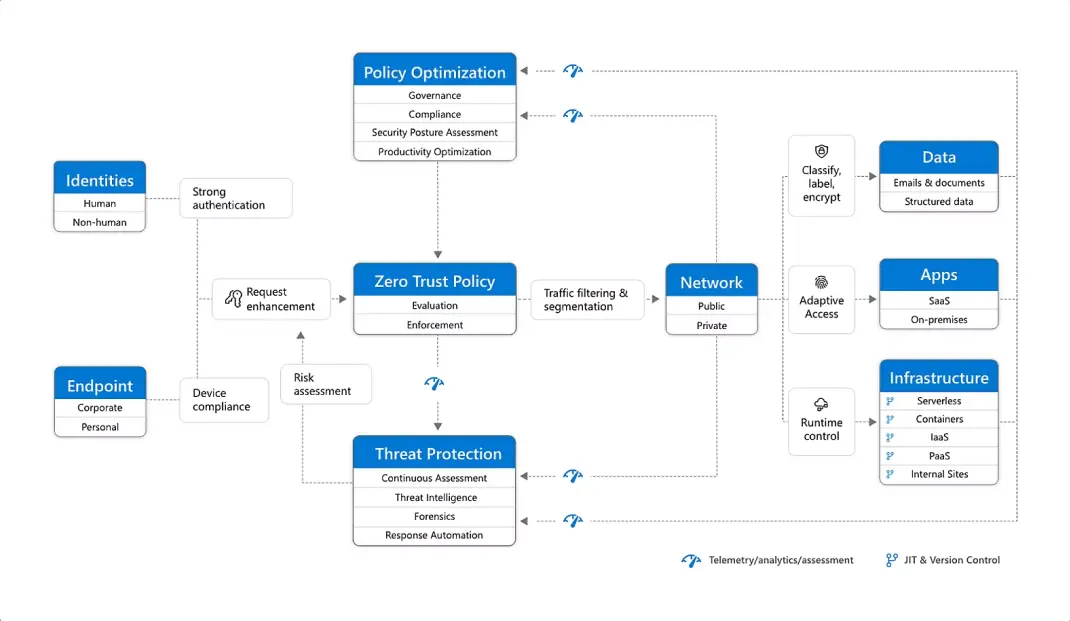
By leveraging Microsoft’s comprehensive suite of security tools and technologies, including Azure Active Directory, Azure Security Center, and Microsoft Defender for Endpoint, CISO Online™ can establish a Zero Trust architecture that safeguards your organisation’s digital assets.
Entra ID (formerly known as Azure Active Directory) provides identity and access management capabilities, allowing us to authenticate and authorise users and devices with precision. Azure Security Center offers advanced threat protection, enabling us to detect and respond to security threats across your environment. Microsoft Defender for Endpoint delivers endpoint security solutions, ensuring that your devices are protected against malware, ransomware, and other cyber threats.
With CISO Online’s integration of Microsoft products, we can implement Zero Trust principles effectively, minimising security risks and providing unparalleled protection for your organisation’s data, applications, and infrastructure.
Partner with us to leverage the combined expertise of CISO Online and Microsoft, and fortify your cybersecurity defences with Zero Trust solutions tailored to your needs.
Connect with our skilled cybersecurity team to fortify your organisation against cyber threats and ensure robust protection for your identity, data, and digital assets. Learn how CISO Online™ utilises these strategies to safeguard your organisation’s digital landscape today
Zero trust is a modern security strategy based on the principle never trust, always verify. Instead of assuming everything behind the corporate firewall is safe, the Zero Trust model assumes breach and verifies each request as though it originates from an open network.
The three main pillars of Zero Trust are:
1. Verify explicitly: always authenticate and authorize based on all available data points, including user identity, location, device health, service or workload, data classification, and anomalies.
2. Use least-privilege access: limit user access with just-in-time and just-enough-access, risk-based adaptive polices, and data protection to help secure data and improve productivity.
3. Assume breach: verify end-to-end encryption and use analytics to gain visibility, detect threats, and improve defenses.
Organisations need Zero Trust solutions because security has become more complex. As increasing numbers of employees work remotely, it’s no longer sufficient to just protect the network perimeter. Organisations need adaptive solutions that fully authenticate and verify every access request and quickly detect and respond to threats both inside and outside the network.
Zero Trust helps solve the problem of greater complexity. Today’s organizations need to protect a growing volume of data across a multiplatform, multicloud environment. Risks to that data have increased as more companies turn to hybrid work and attacks become more sophisticated. Zero Trust helps simplify security with a strategy, processes, and automated tools that verify every transaction, enforce least-privilege access, and apply advanced detection and response to threats.
A Zero Trust network fully authenticates, authorizes, and encrypts every access request, applies microsegmentation and least-privilege access principles to minimize lateral movement, and uses intelligence and analytics to detect and respond to anomalies in real time.
Traditional security models often rely on a secure perimeter (firewalls, VPNs) to protect the internal network. Zero Trust assumes the network is always at risk and requires verification and monitoring regardless of location.
One of the most effective Zero Trust policies is multifactor authentication. Requiring that every user perform two or more forms of authentication (such as using a PIN on a known device) every time they sign in significantly decreases the risk that a bad actor with stolen credentials will gain access.
Implementing a Zero Trust strategy starts with identifying business priorities and gaining leadership buy-in. It may take many years to complete the rollout, so it helps to start with easy wins and prioritize tasks based on business goals. An implementation plan will typically include the following steps:
Roll out identity and device protection, including multifactor authentication, least-privilege access, and conditional access policies.
Enroll endpoints in a device-management solution to ensure devices and apps are up to date and meet organizational requirements.
Deploy an extended detection and response solution to detect, investigate, and respond to threats across endpoints, identities, cloud apps, and emails.
Protect and govern sensitive data with solutions that provide visibility into all data and apply data loss prevention policies.
The core principles include verifying every access request, enforcing least privilege access, segmenting networks, continuously monitoring and logging activity, and assuming breach.
Secure access service edge (SASE), is a security framework that combines software-defined wide area networking (SD-WAN) and Zero Trust security solutions into a converged cloud-delivered platform that securely connects users, systems, endpoints, and remote networks to apps and resources.
Zero Trust, which is a modern security strategy that centers on verifying each access request as though it originates from an open network, is one component of SASE. SASE also includes SD-WAN, Secure web gateway, cloud access security broker, and firewall as a service, all centrally managed through a single platform.
A virtual private network (VPN) is a technology that enables remote employees to connect to the corporate network.
Zero Trust is a high-level strategy that assumes that individuals, devices, and services that are attempting to access company resources, even those inside the network, cannot automatically be trusted. To enhance security these users are verified every time they request access, even if they were authenticated earlier.
Micro-segmentation involves dividing the network into smaller, isolated segments to limit the spread of attacks and restrict lateral movement by attackers within the network.
Technologies include identity and access management (IAM), multi-factor authentication (MFA), encryption, endpoint detection and response (EDR), network segmentation, and security information and event management (SIEM) and etc.
Zero Trust reduces the risk of insider threats by continuously monitoring user activity, enforcing strict access controls, and detecting and responding to unusual behavior.
Yes, Zero Trust can be implemented in cloud environments by using cloud-native security tools, applying strong access controls, and continuously monitoring cloud activity.
Zero Trust secures remote work by verifying the identity and health of remote devices, enforcing least privilege access, and ensuring secure access to corporate resources regardless of location.
Challenges include the complexity of transitioning from legacy systems, the need for cultural change, the potential for initial productivity impacts, and the requirement for continuous monitoring and management.
Zero Trust can complement existing security frameworks by enhancing their effectiveness with continuous verification, segmentation, and real-time monitoring.
Automation helps enforce Zero Trust principles by streamlining processes like identity verification, access control, threat detection, and incident response, reducing human error and improving response times.
Effectiveness can be measured through metrics such as the reduction in successful attacks, improved incident response times, compliance with security policies, and user satisfaction.
Industries handling sensitive data, such as finance, healthcare, government, and technology, benefit significantly from Zero Trust due to their higher risk profiles.
While Zero Trust can initially introduce additional verification steps, it can ultimately enhance user experience by providing secure and reliable access to resources from any location.
Future trends include the increased use of artificial intelligence and machine learning for threat detection, deeper integration with cloud and hybrid environments, and the development of more user-friendly security solutions.

